Below, we offer a brief overview on where to start with auditing your data and authentication strategies to adopt. To access the full guide with more details, recommendations, best practices, and case studies, download the Sell Side Guide to Identity here.
Why Authenticated Audiences Are the Future
As the digital landscape evolves beyond third-party cookies and universal identifiers, authenticated users are becoming publishers’ most critical asset. Logged-in and known audiences enable better targeting, more accurate measurement, and stronger advertiser demand. With authenticated users, publishers have access to rich first-party data that can be consistently tied to a single individual across sessions and devices, enabling deeper user profiles and long-term engagement. This level of transparency and consented data usage also allows publishers to deliver relevant content and advertising experiences, which drives higher user satisfaction and improved campaign performance.
To succeed in this shift, publishers must take ownership of their identity strategy. This means proactively defining how user data is collected, governed, and activated across the organization rather than relying on legacy systems or third-party partners to fill in the gaps. But before jumping into new tools or platforms, it's essential to fully understand the current state of your data. Without a clear picture of where your data lives and how it's managed, even the best identity strategy will fall short. Learn the first steps to take when building an identity graph.
Laying the Groundwork: Audit, Organize, and Close the Gaps
A successful identity framework starts with foundational work. You need a clear understanding of what data you have, where it's stored, and how it can be activated.
1. Locate and Organize Data
Start by mapping your data ecosystem. Identify the following:
- Which platforms collect and store your audience data
- What tools manage it (CRM, CMS, analytics, etc.)
- Where silos exist across departments or vendor systems
Once documented, consolidate your data into a centralized repository—whether it’s your own data warehouse or through a specialized platform provider. This unified foundation will power your identity graph and activation strategy. By bringing all relevant data sources into one place, publishers can reduce silos, improve data accuracy, and enable faster access for downstream tools such as customer data platforms, ad servers, and analytics systems.
2. Evaluate Identifiers and Their Usability
Not all identifiers are equally valuable or interoperable. Focus on those that are deterministically acquired and portable across environments. Deterministic identifiers such as email addresses and login IDs provide a higher level of accuracy and reliability compared with probabilistic or inferred IDs. Ensuring portability across devices, platforms, and partners allows for seamless audience targeting and measurement. By auditing both collected first-party and licensed data, you can identify which identifiers are most usable and where you have gaps.
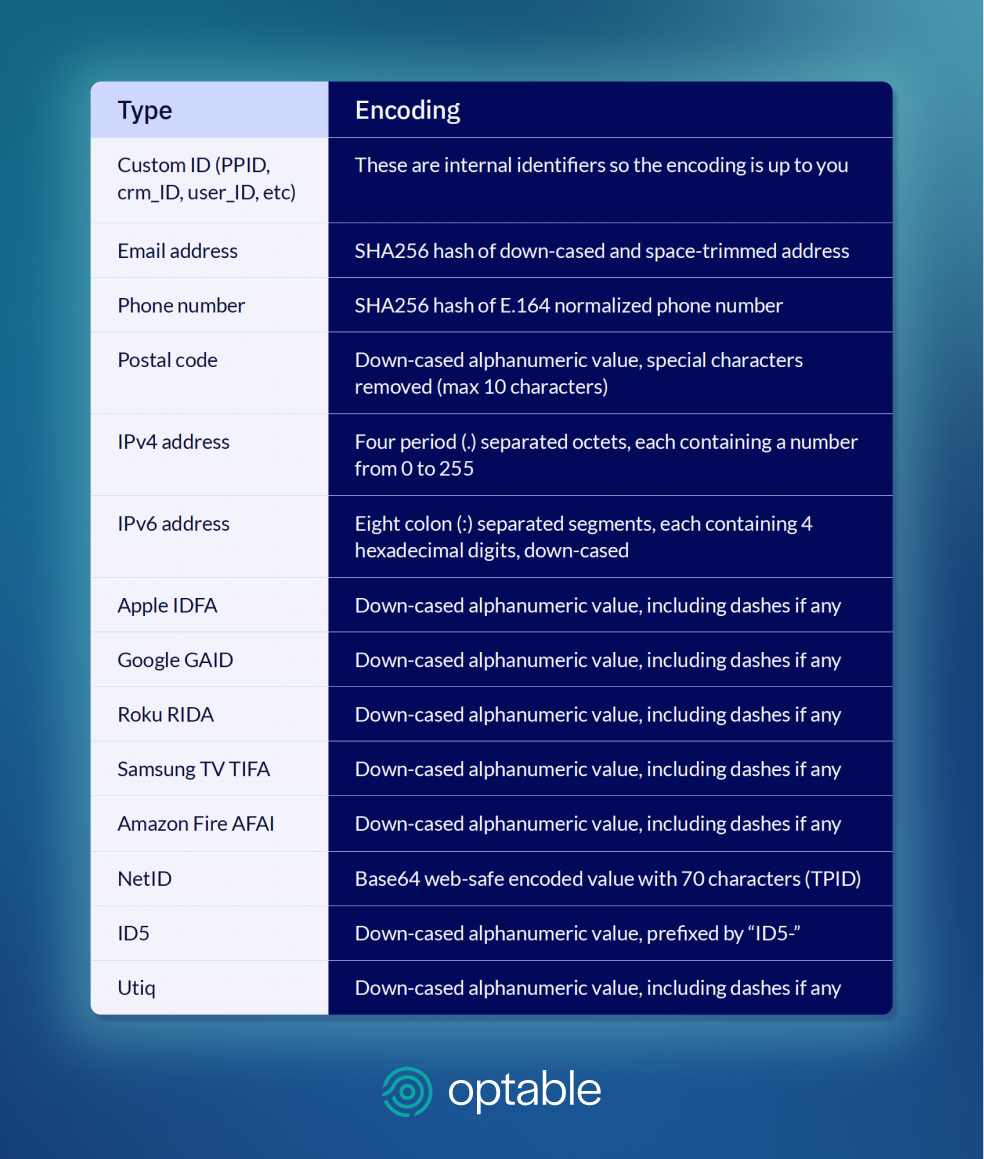
3. Understand Identity Gaps
Assess how much of your audience is already identifiable. It is important to determine the share of authenticated users with usable first-party identifiers and the portion of anonymous or unmatchable users. Those who engage with your content but cannot yet be tied to a verified identity can reveal gaps in your data collection and opportunities to convert them into known users.
This gap analysis is critical in shaping both your short-term activation strategy and your longer-term authentication approach, as it highlights where your current data falls short, which user segments are underrepresented, and which identifiers need strengthening. By understanding these gaps, you can prioritize immediate actions to better engage identifiable users while simultaneously planning initiatives that will increase authenticated user coverage over time.
Growing Authenticated Engagement
With identity gaps identified, publishers can focus on expanding their base of known users through smart, user-friendly engagement strategies. Below are a few examples.
Authentication Tactics That Work
- Platform Logins
Offer login options via trusted platforms like Google, Apple, or Facebook for easy access and high-quality data capture. - Premium Subscriptions
Use content gating or service upgrades to encourage subscriptions and collect reliable identifiers. - Email Subscriptions
Capture email addresses through newsletters or updates. These opt-ins provide a consistent and high-value ID for identity graphs. - Contests & Gated Experiences
Run interactive campaigns like sweepstakes, polls, or fantasy leagues that require login or registration. These help expand your known audience with minimal friction.

Learn More: The Sell Side Guide to Identity
The steps outlined here are just the starting point. For a more in-depth understanding on how to enhance identity strategies, explore Optable’s Sell Side Guide to Identity, which includes:
- Practical frameworks for auditing and organizing data
- A breakdown of identity technologies and clean room infrastructure
- Audience monetization strategies for both programmatic and direct sales
- Examples of how publishers are executing high-ROI identity strategies
- Checklists to get your identity project off the ground
📥 Download the guide and start building your own future-proof identity strategy today.

.jpg)

.png)
.png)




